- Topic1/3
6k Popularity
26k Popularity
10k Popularity
5k Popularity
171k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is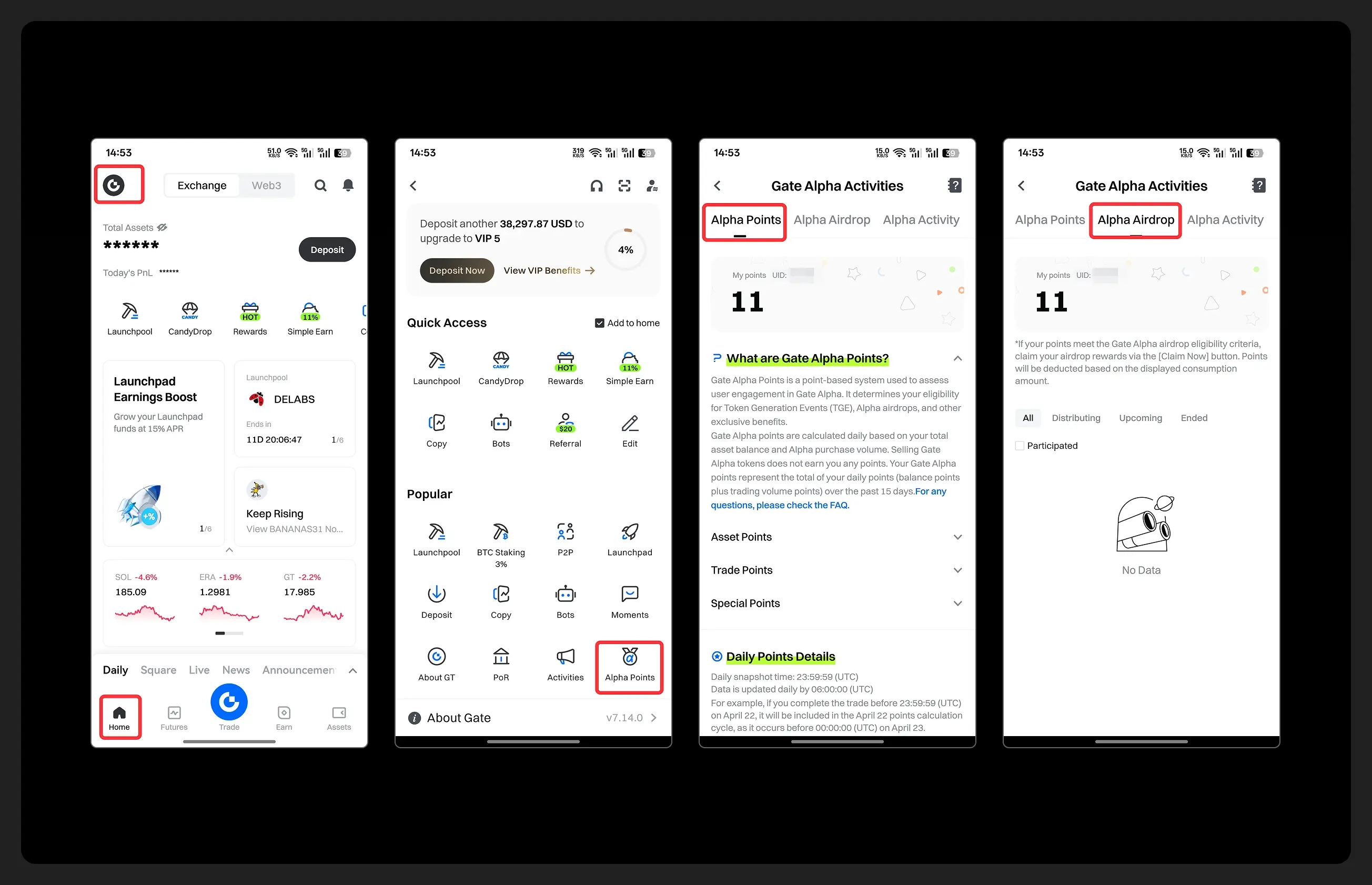
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
Cork Protocol Hacker attack caused losses exceeding 12 million USD, in-depth analysis of the reasons and process.
Analysis of the Cork Protocol Hack: Losses Exceed 10 Million USD
On May 28th, a security incident targeting the Cork Protocol drew widespread attention in the industry. After the incident occurred, Cork Protocol quickly took action, suspending all market transactions to prevent further risk expansion. The security team immediately launched an investigation, and here is a detailed analysis of the attack.
Event Background
Cork Protocol is a tool that provides depeg swap functionality for the DeFi ecosystem, aimed at hedging the depegging risks of pegged assets such as stablecoins, liquid staking tokens, and RWAs. Its core mechanism allows users to transfer price volatility risks to market participants through trading risk derivatives, thereby reducing risks and enhancing capital efficiency.
Reason for Attack
There are two fundamental reasons for this attack:
Cork allows users to create redemption assets using any asset through the CorkConfig contract (RA), enabling attackers to use DS as RA.
Any user can call the beforeSwap function of the CorkHook contract without authorization and allow custom hook data to be passed in for CorkCall operations. This enables attackers to manipulate DS in legitimate markets, deposit it into another market as RA, and obtain the corresponding DS and CT tokens.
Attack Process
The attacker first purchases weETH8CT-2 tokens with wstETH on the legitimate market.
The attacker created a new market, using a custom Exchange Rate provider, with weETH8DS-2 tokens as RA and wstETH as PA.
The attacker adds liquidity to the new market, enabling the protocol to initialize the corresponding liquidity pool in Uniswap v4.
By utilizing the unlockCallback function during the unlocking of the Uniswap V4 Pool Manager, the attacker calls the beforeSwap function of CorkHook and passes in custom market and hook data.
The CorkCall function trusts the data passed in by the legitimate CorkHook from the upper layer and executes it directly, allowing attackers to transfer the legitimate weETH8DS-2 tokens from the market into the new market as RA, and obtain the corresponding CT and DS tokens from the new market.
The attacker redeems RA tokens (i.e., weETH8DS-2 tokens) in the new market using the acquired CT and DS tokens.
Finally, the attacker will match the weETH8DS-2 token with the previously purchased weETH8CT-2 token to redeem wstETH tokens in the original market.
Consequences of the Attack
According to the analysis by the on-chain anti-money laundering and tracking tool MistTrack, the attacker’s address profited 3,761.878 wstETH, worth over $12 million. The attacker then exchanged wstETH for 4,527 ETH through 8 transactions.
As of the analysis, there are a total of 4,530.5955 ETH remaining at the attacker's address. The security team will continue to monitor the flow of funds.
Security Recommendations
To prevent similar incidents from happening again, developers should pay attention to the following points when designing protocols:
This incident once again highlights the importance of security design in DeFi protocols. As the DeFi ecosystem continues to develop, both developers and users need to enhance their security awareness and work together to maintain a healthy and stable ecological environment.